CIS Benchmarks are often regarded as the gold standard for configuring systems safety when securing your Google Workspace environment. These benchmarks provide step-by-step guidance on strengthening your cloud-based infrastructure against potential threats. If you’re unfamiliar with these resources, you can download the latest benchmarks here.
But, even with CIS benchmarks as a foundation, some critical vulnerabilities and misconfigurations remain overlooked. Misconfigurations and overlooked settings—like Google Groups permissions, public Google Spaces, or the absence of Chrome reporting—can leave your organization vulnerable to data breaches, compliance failures, and insider threats.


In this article, we’ll walk through common security gaps, explain why they matter, and give you step-by-step fixes to ensure your Google Workspace is as secure as possible. Let’s get started—because securing the basics isn’t just about ticking boxes, it’s about protecting what matters most.
From Gaps to Guarded — Let Us Protect Your Workspace 24/7
Misconfigured Google Groups for Business
Google Groups for Business is an incredibly versatile tool that enables streamlined communication and group management within your organization. However, when misconfigured, it can create a significant security gap.
By default, group conversations may be accessible to non-members and, in some cases, even individuals outside your organization. It opens the door to data breaches as confidential conversations, such as recruitment details (e.g., CVs, salary offers) or internal project updates, could be exposed.
How to fix it:
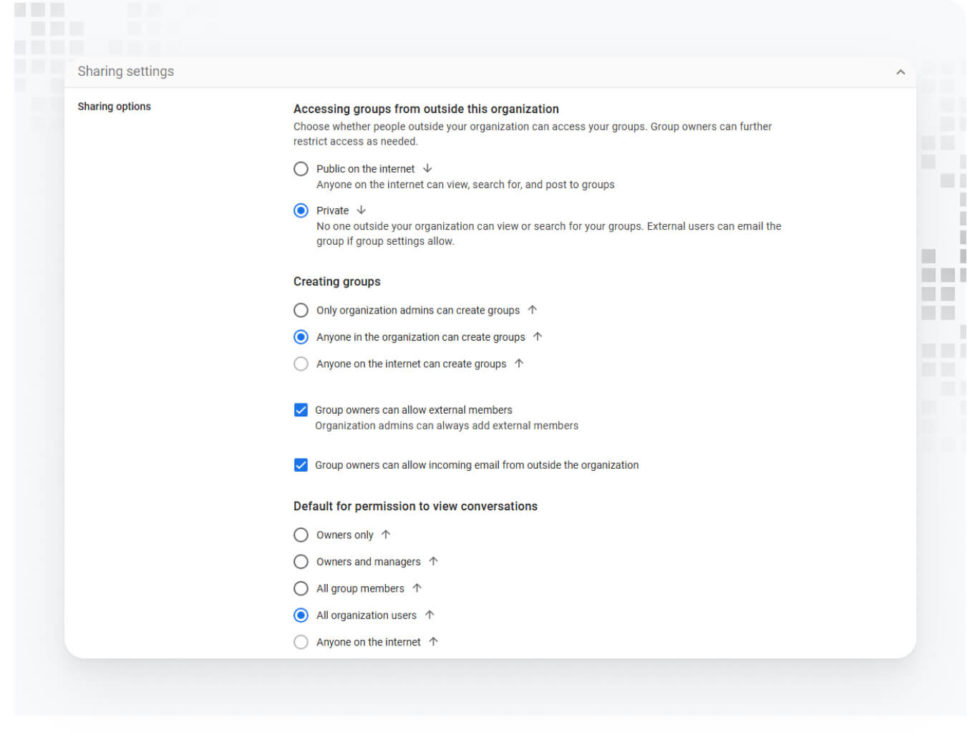
- Restrict default permissions for viewing conversations to group members only:
- In the Google Admin Console, go to Apps > Google Workspace > Groups for Business.
- Under Sharing options, set the Default for permission to view conversations to All group members.
- Lockdown external access: Set Accessing groups from Outside this organization to Private.
- Restrict the creation of new groups to organization administrators:
- Under Creating Groups, select Only organization admins can create groups.
- Click Save.

Note: Changes to default settings do not retroactively apply to existing groups. To address this:
- Visit Google Groups as an administrator.
- Click All Groups.
- Update settings under Group Settings > General to ensure compliance for each group

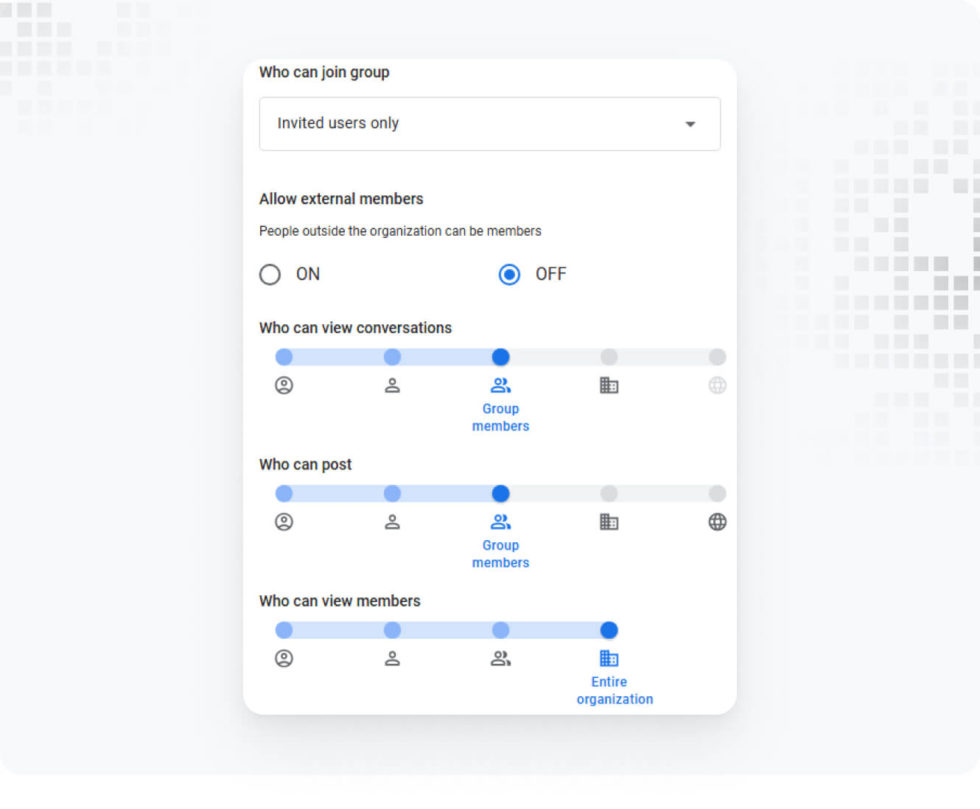
Public Google Spaces
Google Spaces can be a powerful tool for internal collaboration. However, if left open to public access, they can become another vector for data exposure.
How to fix it
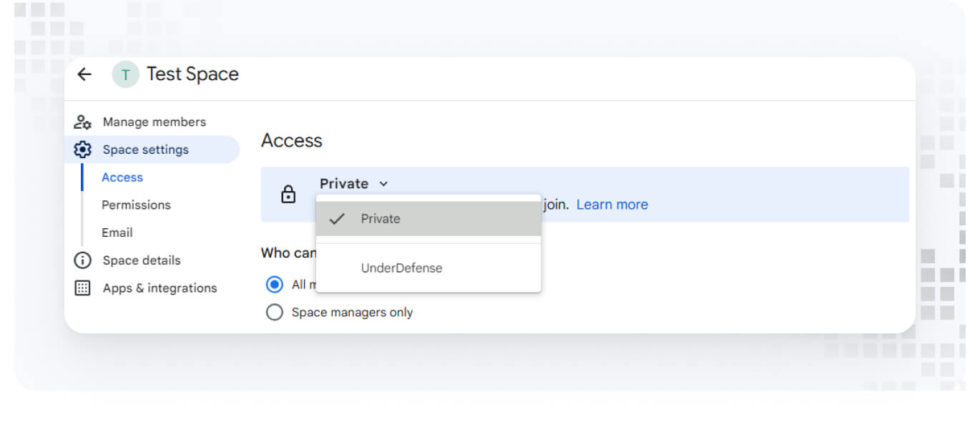
- Set spaces to Private.
- Open Gmail, and navigate to Chat.
- Select a Space and click its name at the top.
- Under Space settings, set Access to Private.
- Educate Teams: Ensure all employees understand the importance of using private Spaces for sensitive communications.

Secure Your Google Workspace—We’ll Handle the Rest
Chrome Events Reporting
Chrome Enterprise offers robust reporting features that provide deeper visibility into user activity. Leveraging these features can help organizations enhance security and gain valuable insights.
Benefits of Chrome Events Reporting
- User Activity Visibility: See which files are downloaded, who installs which extensions, and where sensitive information is being entered.
- Improved Threat Detection: Track potentially risky actions such as sharing sensitive files externally or uploading to unauthorized platforms.
- Extension Management: Identify and control the extensions users install, ensuring compliance with security policies.
How to Set Up Chrome Events Reporting
- Go to Google Admin Console.
- Select Chrome Browser > Setup Guide > Start walkthrough.
- Follow these steps:
- Select the organization unit.
- Enable Managed Browser Cloud Reporting to collect browser version details, user profile data, and information on installed extensions.
- Enroll browser.
Note: This step is optional, as basic event reporting works without device enrollment, but enrolling provides additional visibility and control. - Apply relevant Chrome policies based on organizational needs.
- Manage extensions by setting blocklists, allowlists, or enforcing mandatory installations.
- Configure Browser Reporting:
- Go to Google Admin Console > Devices > Chrome > Settings.
- Under User & Browser Settings > Browser Reporting, click Edit in legacy view and enable Event Reporting, select all event types for comprehensive visibility.
Security Insights
Chrome’s Security Insights feature helps monitor insider risks and data loss. It highlights users frequently downloading sensitive documents or sharing files externally, across various platforms. These insights can include:
- File download activity.
- Data is pasted into tools like ChatGPT or shared on external sites.
- Extension-related risks.

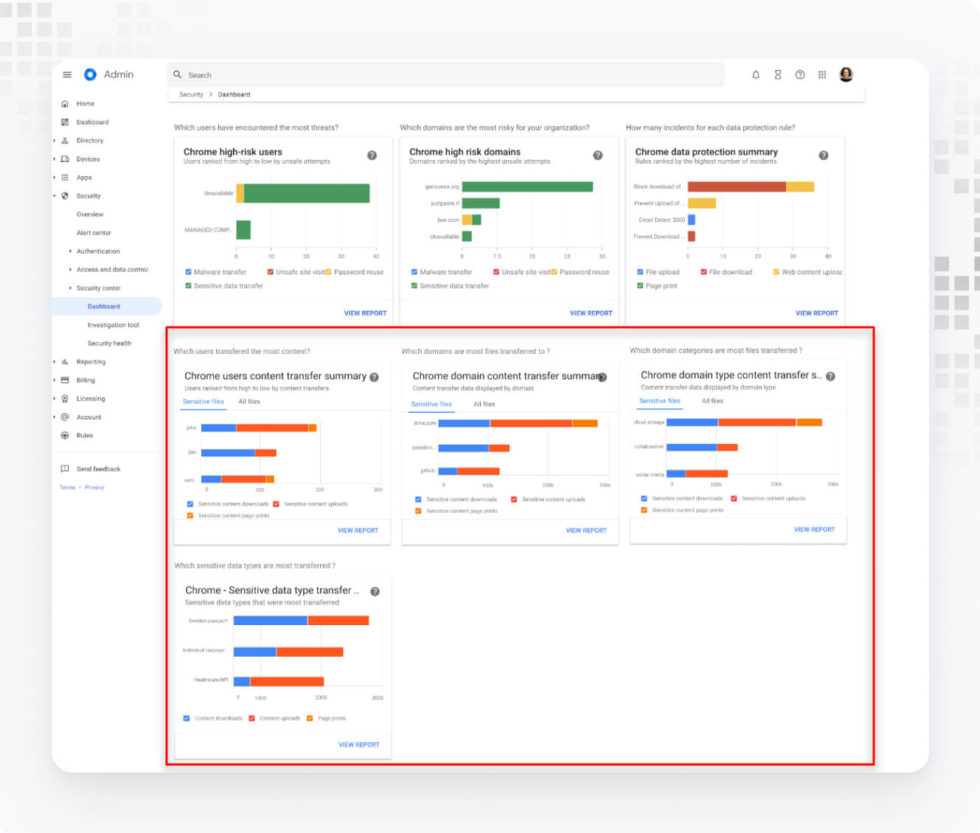
All events related to Google Chrome can be viewed under Security > Investigation Tool, selecting Chrome events as the data source.
Note: To log these activities, users must be signed into a dedicated Chrome profile using their organization’s domain account.
For better incident management and advanced threat monitoring, integrating these logs with a 24/7 security automation and compliance solution or SOC as a service ensures timely incident detection and response.
Your Google Workspace Deserves 24/7 Protection — Let’s Make It Happen
Need help? We’ve got you covered
The configurations and practices highlighted here are just the beginning. A thorough security assessment can uncover deeper risks and provide tailored solutions for your environment. At UnderDefense, our security experts specialize in evaluating cloud platforms like Google Workspace, Amazon Web Services, Microsoft 365, Microsoft Entra ID, and Google Cloud Platform. We’ll identify vulnerabilities, compare your setup to industry benchmarks, and deliver actionable recommendations to mitigate risks.
Why Choose Us?
- MDR Services: Managed Detection and Response (MDR) provides 24/7 monitoring and rapid incident response. With MDR, you gain access to AI-powered threat detection and expert human analysis.
- vCISO Services: Virtual Chief Information Security Officer (vCISO) services help streamline compliance, automate processes, and free up your team to focus on core business goals.
- SOC Outsourcing: A Managed SOC (Security Operations Center) ensures round-the-clock monitoring—offering full protection without the operational burden of an in-house team.
“If I had to choose between outsourcing a SOC or going with MDR, I’d pick MDR. It’s often cheaper but just as effective. Plus, MDR gives you more flexibility—custom detection, faster response times, and way less noise in alerts.”
— Matthew Sciberras, CISO-VP of Information Security at Invicti Security
1. In which subscription levels are Google Workspace settings available?
Chrome Event Reporting and Settings for Google Spaces and Google Groups are available across all subscription levels, starting from Business Starter.
2. What types of events can Chrome Event Reporting track?
Chrome Event Reporting can track events such as downloaded/uploaded files, installed extensions, sensitive data sharing, password reuse, and more across all websites.
3. Can I integrate Chrome logs into SIEM systems?
Yes, you can integrate Chrome logs into SIEM systems by using the Connectors feature under Chrome > New Provider Configuration to set up the SIEM integration.
4. Do I need to enroll devices for Chrome Event Reporting?
No, basic event reporting works without device enrollment, but enrolling provides additional visibility and control. To report these types of activities, users must be signed into a dedicated Chrome profile using their organization’s domain account.
5. Does UnderDefense allow monitoring Chrome Event logs and other types of Google Workspace logs?
Yes, UnderDefense can monitor Chrome Event logs and other Google Workspace logs as part of our Managed SOC or MDR services. This enables enhanced threat detection by tracking activities like data exfiltration, policy changes, unauthorized access, etc.
6. What are Google Workspace security best practices?
To secure Google Workspace:
- Set Spaces to Private: Grant access to invited members only.
- Restrict Access to Google Groups: Limit visibility of group conversations.
- Enable Chrome Events Reporting: Monitor browser activity for security risks.
For more best practices on securing Google Workspace, check out our guide: Google Workspace Security Best Practices.













