Regarding protecting a business, there’s a common myth that a Support team or Network Operations Center (NOC) can handle security. But here’s the truth: NOC vs SOC isn’t just a difference in acronyms—it’s a difference in purpose. Security isn’t the same as support tickets or network uptime. Security requires specialized knowledge, tools, and a whole different mindset. Let’s dive into what makes a SOC (Security Operations Center) unique and why you shouldn’t rely on your NOC or Support teams to handle security threats.
What is a NOC?
First, don’t get me wrong: the NOC is vital. Without it, your corporate network might run like a car with a flat tire—technically functional, but not getting anywhere fast.
The NOC is essentially the nerve center of your organization’s IT infrastructure. This team ensures your corporate network is always up and running and optimized to meet your business needs. Think of them as your network’s mechanics and pit crew—if something’s not performing as it should, they’re the ones troubleshooting, tuning, and patching to keep it humming.
What do they do?
- Monitor for downtime.
- Troubleshoot connectivity.
- Optimize resources for smooth operation.
- Do routine maintenance so things run like a well-oiled machine.
In short, the NOC gives your business the digital roads to get where you need to go.
What is a SOC?
Now, let’s switch. While the NOC ensures the digital roads are smooth, the SOC makes sure they’re not full of potholes or under attack by cyber thieves.
The SOC is your cybersecurity castle. These analysts work 24/7, protecting your organization’s digital assets from cyber threats. Their round-the-clock vigilance should make you feel secure. They’re not just responding to attacks; they’re proactively building the walls to prevent them in the first place. If something does get through—because let’s be real, no system is 100% foolproof—they’re the first responders to detect, analyze, and mitigate.
Here’s what they do:
- Monitor for cyber threats in real time.
- Perform incident detection, analysis, and response.
- Harden systems to prevent vulnerabilities.
- Proactively hunt for threats before they strike.
Whether your SOC is in-house or provided by a third-party SOC as a Service, their mission remains to keep your organization’s digital assets safe from harm.
Endpoints Are Just the Beginning.
Protect more than endpoints—secure your entire network, cloud, and beyond with expert-driven 24/7 monitoring and threat-hunting
SOC vs NOC: What are the key differences?
So, is it NOC or SOC? The answer is both! While they might work side by side, their focus areas differ vastly. As crucial as Support teams are, security challenges fall well outside their scope. We all know what support teams are supposed to do—troubleshoot client issues and ensure things are working smoothly.
Let’s break down the key differences between NOC, SOC, and Support teams by examining their primary focus, core responsibilities, skills, and tools they use.
|
NOC (Network Operations Center) |
Network & Infrastructure Monitoring |
Ensuring network uptime, monitoring infrastructure, resolving network-related issues |
Network monitoring tools like SolarWinds, Nagios |
Strong troubleshooting, network optimization, and infrastructure management skills |
|
SOC (Security Operations Center) |
Cybersecurity Threat Detection & Response |
Monitoring for cyber threats, detecting and responding to security incidents, investigating breaches |
SIEM (Splunk, QRadar), EDR (CrowdStrike, SentinelOne), Threat intelligence |
Advanced threat analysis, incident response, and proactive threat-hunting skills |
|
Handling user requests, troubleshooting, and customer queries. Resolves issues but does not focus on security threats. |
Ticketing systems like Zendesk, ServiceNow |
Customer service, technical troubleshooting, and effective communication skills |
Why a NOC or IT Support fail your security
Many companies try to save money by relying on their NOC or 24/7 IT Support instead of building a full-fledged security function. The assumption? Their existing tools—Cloud, SaaS, Email, Identity, Endpoint, Vulnerability Management, Kubernetes, and more—will send alerts to Slack or another channel, and someone will act on them.
But here’s the problem: this approach often results in alert fatigue and critical gaps in protection. Why?
- Tools are left untuned. They flood the system with noise, leading to alerts being ignored or outright silenced (e.g., kill/whitelist strategies).
- Security expertise is absent. Support teams aren’t equipped to handle complex security tasks like assessing consequences, understanding MITRE techniques, investigating incidents, or responding to threats effectively.
- Compliance suffers. Without centralized visibility, critical gaps are overlooked—often only flagged during audits.
- Talent drains away. Skilled staff often leave for specialized security roles, where the work is more rewarding, and the pay is better (especially for night shifts).
Case in point: Uber. When an attacker compromised AWS and SentinelOne, no dedicated team detected and responded to the breach in time.


Here, we present 5 reasons, clearly explaining why a SOC is not the same as a NOC and not just another IT support team.
1. Focus on cybersecurity
- NOC: Ensures systems stay up and running, monitors network health, and keeps the servers from crashing.
- SOC: Operates with a different goal—finding and stopping threats before they impact the organization. The SOC’s priority is protecting data, preventing breaches, and keeping cyber adversaries at bay. They don’t just handle issues; they actively hunt for potential threats.
- Support team: Focuses on user issues and technical assistance. Think of them as the “first responders” for routine tech problems.
2. Specialized skills in threat detection and response
SOC analysts are trained to understand attack vectors, identify malware signatures, and analyze threat patterns. Unlike the NOC, they don’t just monitor service outages—they’re constantly looking for suspicious activity.
They use Security Information and Event Management (SIEM) like Splunk or QRadar to analyze logs for unusual patterns, Endpoint Detection and Response (EDR) tools like SentinelOne or CrowdStrike EDR to detect endpoint threats, and threat intelligence platforms to stay ahead of emerging risks.
3. A tiered approach to security
SOC teams are structured in a tiered format, with each level handling specific aspects of threat management:
- Tier 1 (Security analysts): Handle initial alerts, investigate incidents, and gather evidence.
- Tier 2 (Incident responders): Respond to and contain security incidents, perform deeper investigations, and validate alerts.
- Tier 3 (Threat hunters): Proactively hunt for hidden threats, identify vulnerabilities, and support ongoing threat intelligence efforts.
This structure ensures that incidents are managed efficiently, escalations are handled correctly, and threat intelligence is actively used to strengthen security.
4. SOC Principal & SOC Manager – Leaders, not supervisors
- The SOC Principal and SOC Manager play critical roles in shaping the strategy, processes, and roadmap for the entire security posture. They aren’t just supervisors but are responsible for creating automation playbooks, developing operational rules, and continuously improving the organization’s security readiness.
- Support and NOC teams typically have supervisors and managers focused on SLA adherence, customer satisfaction, and network uptime—not proactive security management.
5. Proactive threat hunting vs. reactive issue resolution
While Support and NOC teams are reactive (they respond to requests or downtime issues), the SOC is proactive. Tier 3 SOC analysts, known as threat hunters, constantly look for indicators of compromise (IOCs), test new detection methods, and identify emerging threats before they can impact the organization.
Got a SOC? Make sure it’s not a Schrödinger Cat SOC
Your SOC exists, but is it alive or dead? The answer depends on its effectiveness, and here’s where the magic—or chaos—happens. Let’s break down the “Schrödinger SOC” conundrum into four stages that reflect the lifecycle of your security operations and what needs to happen at each step.
Stage 1: Feed the right data – Don’t dump junk
Let’s be real: your EDR or SIEM tool is like a Michelin-star chef—it can create masterpieces, but only if you give it the right ingredients. Feed it garbage data and you’ll get a dish that even your SOC team won’t save.
Here’s the deal: not all logs are created equal. You need to identify the ones that matter—endpoint telemetry, network traffic, and cloud activity—and leave out the junk that fills your system. Otherwise, you’re trying to find gold in a landfill. Once you have the good stuff, turn on the right detections so your SIEM knows what to look for.
Pro tip: Curate your data sources like you’re shopping for the finest produce at the market.
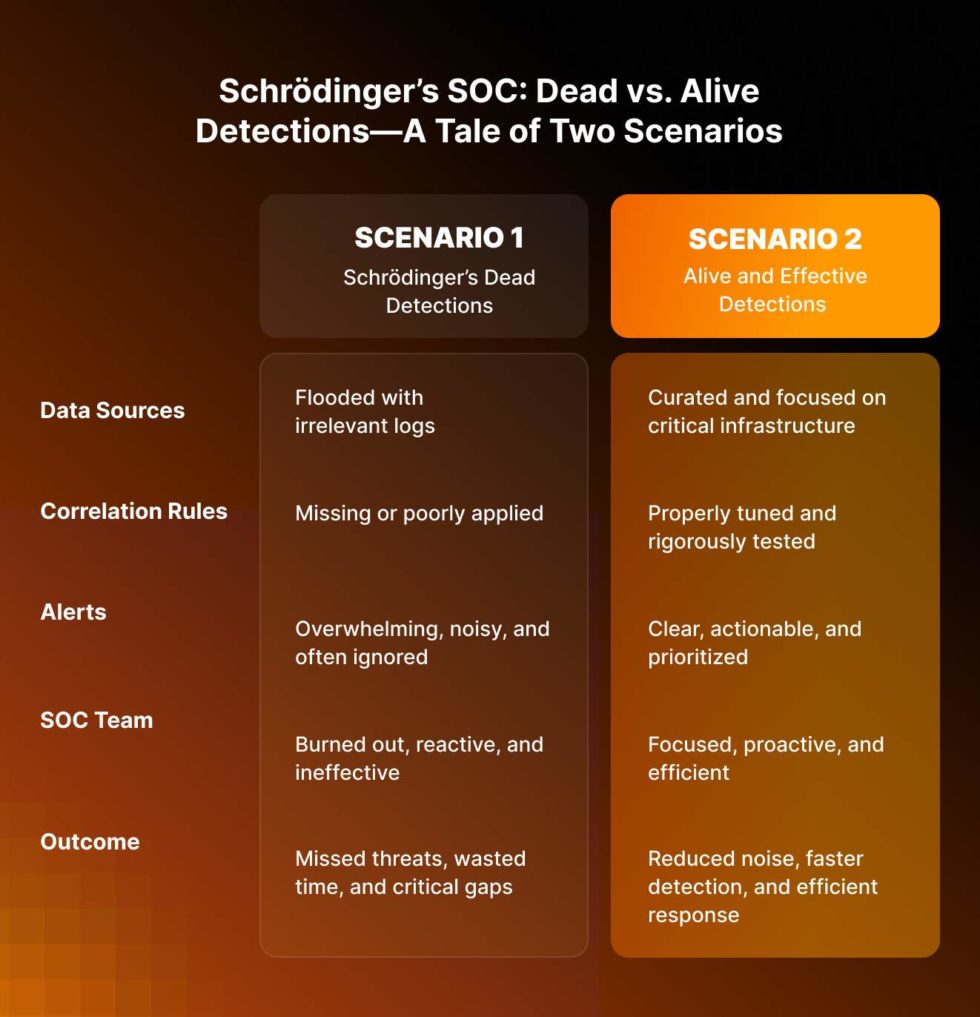
Stage 2: Schrödinger’s detections – Two scenarios, two fates
Your SIEM is like Schrödinger’s cat—it can be alive and effective or dead and useless and you won’t know which until you open the box. The difference is whether you set it up or just hoped for the best.
Scenario 1: The Schrödinger’s cat disaster (dead detections)
Imagine dumping all your logs into your SIEM without a care, like throwing all the spices in the cabinet into the soup. What do you get? Chaos. Your SOC team is buried under:
- Noise overload: False positives and irrelevant alerts as far as the eye can see.
- Critical gaps: Threats slipping by like thieves in the night.
- Burnout: Your analysts are about to quit because they’re fighting a losing battle with irrelevant alerts.
It’s a recipe for disaster. Your SIEM exists but it’s dead when you need it most.
Scenario 2: The right path (alive and effective detections)
Now imagine this: You curate your data, so only the logs that matter are fed into your SIEM. You apply correlation rules, tune detections, and then test detections and rules thoroughly. What do you get?
- Handy alerts: Your team only gets the pings that matter. No junk, no spam, just the good stuff.
- Efficient operations: Your SOC analysts are solving mysteries not sorting through mountains of noise.
- Proactive defense: Simulated attacks prove your system works and gaps are patched before attackers find them.
Pro tip: Think of this like brewing the perfect cup of coffee—grind the beans, use the right water temperature and taste-test every step of the way. Test detections rigorously, using simulated attacks, red teaming, and adversary emulation to validate that detections trigger as expected.
Schrödinger’s SOC: Dead vs. Alive Detections—A Tale of Two Scenarios

Stage 3: Optimize for impactful findings
Even the best SIEM is like a sports car—it needs a skilled driver, regular tune-ups, and the right fuel to go fast. This is where your engineers come in, creating an environment where analysts can do their job without wanting to pull their hair out.
By reducing false positives and designing clear and impactful alerts, you give your SOC team the tools to respond fast and effectively. Think of it as turning a messy garage into a Formula 1 pit stop—everything is streamlined, efficient, and ready to go.
Pro tip: Eliminate noise, focusing on quality over quantity to reduce false positives and SOC fatigue. The faster your analysts can respond the less likely you’ll be in the headlines for all the wrong reasons.
Stage 4: Proactive monitoring and threat hunting
Finally, we reach the nirvana of a mature SOC: proactive threat hunting. Instead of playing whack-a-mole with alerts your SOC team can now focus on hunting down threats before they strike.
It’s like turning your SOC from a fire department that only responds when there’s smoke into an elite detective agency that catches arsonists before they light the match. This is where you get ahead of the game, using your finely tuned SIEM and top-notch analysts to find trouble before it becomes an incident.
Pro tip: If this sounds like climbing a mountain, consider a SOC-as-a-Service. They’ll bring the expertise, tools, and processes to get you there without the headache.
Managed SOC – Key to a MATURE security operation
Building a mature SOC takes more than just tools—it’s about making them work for you. SIEM goes far beyond a proper setup. Managed SIEM services work as part of a broader strategy to help businesses set up, optimize, and operate their security environments effectively.
Managed SOC with 24/7 monitoring, fine-tuning, and noise reduction, is more than monitoring—it’s a true partnership. Think of it as your expert defense team on call, always adapting to your needs. MDR (Managed Detection and Response), is like a SOC on steroids—fast detection paired with rapid responses to bridge the gap between monitoring and action.
Download our guide to learn how to choose the right SOC as a service provider


To top it off, MDR platforms automate detection across the cloud, endpoints, and more, with clear dashboards for full visibility. It’s not just about finding threats but seeing the bigger picture and acting on it effectively.
Stop Fighting Noise, Start Detecting Threats in Minutes
Conclusion
To wrap it up, here’s a quick look at why SOCs are essential and why Support and NOC teams aren’t cut out for this job:
- SOCs specialize in security threats, while Support teams and NOCs handle general IT issues.
- SOCs use advanced tools, SIEMs, EDRs, and threat intelligence platforms to detect and respond to threats in real time.
- SOC teams are structured in a tiered approach with defined roles, from Tier 1 analysts to advanced threat hunters (Tier 3), ensuring incidents are handled efficiently.
- SOC Managers and Principals focus on strategy and process, unlike the typical operational focus of NOC or Support team managers.
- A mature SOC as a service, combines threat-centric expertise, advanced tool optimization, 24/7 monitoring, and strategic oversight to deliver proactive and efficient cybersecurity, while you focus on your business.
1. What are Modern NOC and SOC Challenges?
Modern NOCs face challenges like maintaining uptime, resolving network issues quickly, and optimizing performance under increasing demand. SOCs, on the other hand, grapple with growing alert volumes, advanced cyber threats, and the need for skilled talent to manage complex tools like SIEM and EDR effectively.
2. What do SOCs manage?
SOCs manage the detection, analysis, and response to security threats across an organization’s environment. This includes cloud infrastructure, endpoints, identity systems, email, and more. They ensure risks are identified, triaged, and addressed before they cause damage.
3. Can a NOC or IT Support Team replace a SOC?
No. While NOCs and IT Support handle operational issues, they lack the specialized skills, tools, and processes required to manage security incidents. SOCs are purpose-built to focus on cybersecurity threats.
4. What is SIEM, and why is it important?
SIEM (Security Information and Event Management) is a centralized platform that aggregates, correlates, and analyzes security data from multiple sources. It provides visibility, reduces noise, and enables faster threat detection and response when managed properly.













